HashiCorp Setup
Installing Gloo Gateway will require an environment for installation. In this document we will review how to prepare an environment that uses the HashiCorp family of products for the installation of Gloo Gateway.
Overview
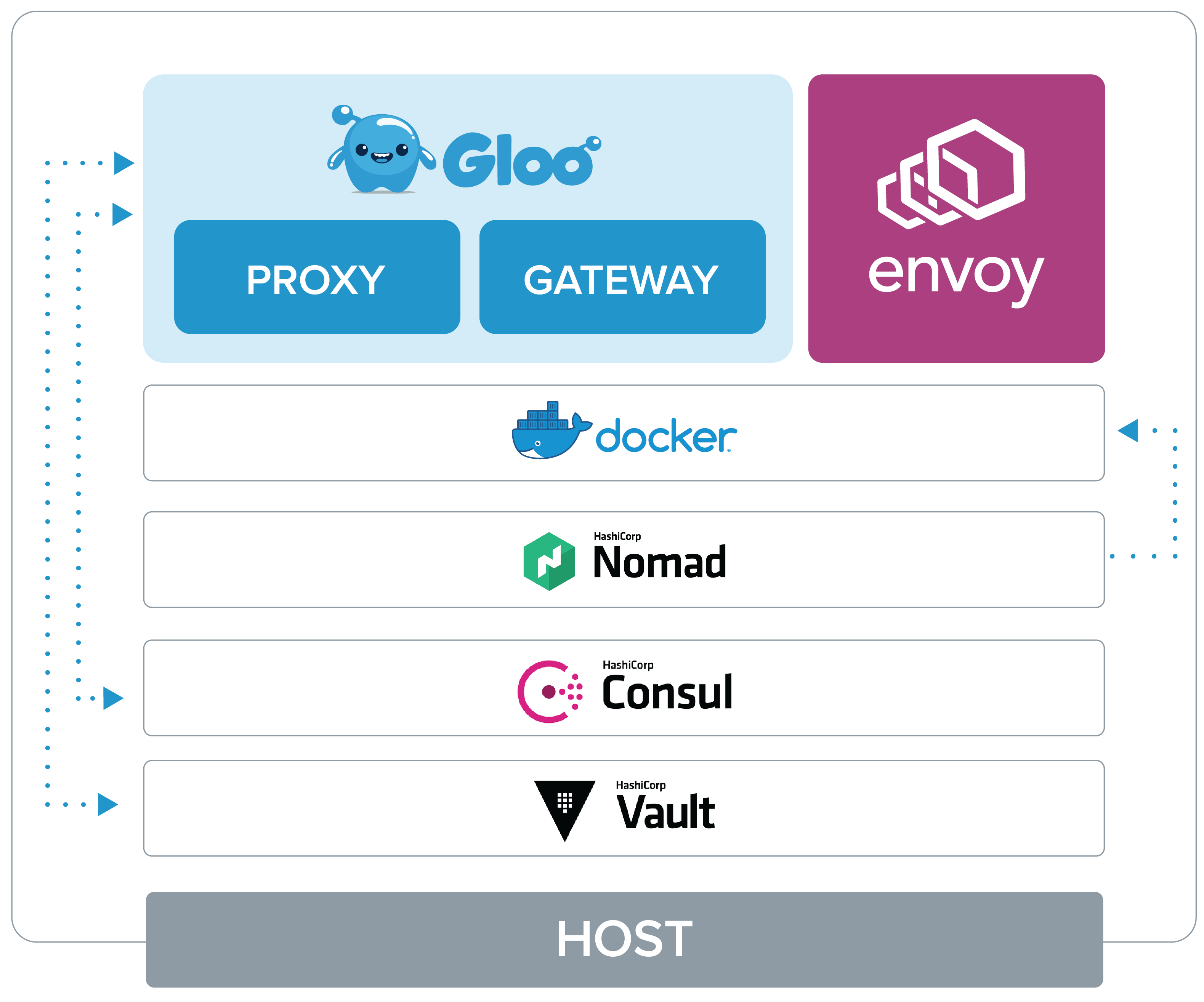
HashiCorp has the following products that can be utilized by Gloo Gateway for different functions:
- Nomad - A simple and flexible workload orchestrator that can deploy the Gloo Gateway containers on managed hosts.
- Consul - A service networking solution that can provide both service discovery and key/value storage for Gloo Gateway.
- Vault - A secrets lifecycle management tool that can provide secure storage of secrets within Gloo Gateway.
Nomad
HashiCorp provides excellent documentation and examples on how to deploy Nomad in a development or production environment. The Nomad agent is installed on nodes that will host workloads deployed by a Nomad job. In the case of Gloo Gateway, the hosts must support the deployment of containers.
You should have the most recent version of Nomad downloaded and the Nomad agent deployed on any worker nodes on which you want to install Gloo Gateway. You can also run Nomad locally in development mode.
Consul
HashiCorp provides documentation and examples on how to deploy Consul in a development or production environment. Consul can be deployed on bare-metal, virtual machines, or containers. It is possible to deploy Consul on Kubernetes, and then use Consul for service discovery and configuration data storage instead of using Custom Resources and Kubernetes service discovery.
You should have the most recent version of Consul downloaded and deployed in a location that is addressable by your target Gloo Gateway environment. Consul and Gloo Gateway do not have to run on the same Nomad nodes or Kubernetes cluster. You can also run Consul locally in development mode.
Vault
HashiCorp provides documentation and examples on how to deploy Vault in a development or production environment. Vault can be deployed on bare-metal, virtual machines, or containers. It is possible to deploy Vault on Kubernetes, and then use Vault for secrets management instead of using Secrets in Kubernetes.
You should have the most recent version of Vault downloaded and deployed in a location that is addressable by your target Gloo Gateway environment. Vault and Gloo Gateway do not have to run on the same Nomad nodes or Kubernetes cluster. You can also run Vault locally in development mode.
Next Steps
Once you have prepared a suitable environment for the deployment of Gloo Gateway on HashiCorp’s products, you can run through the guide for getting Gloo Gateway deployed.
